|
|
Amazon Web Services (AWS) Simple Storage Service (S3) is a widely used object storage service that allows users to store and retrieve data from anywhere on the web. While it is a popular choice for cloud storage, there are several common mistakes that users make when using S3 that can lead to data loss, security breaches, or increased costs. In this blog, we will discuss some common errors you can make while using AWS S3 mistakes and how to rectify them.
Before we start let us first do a quick overview of AWS S3.
Table of Contents
What is AWS S3
Amazon S3 (Simple Storage Service) is a cloud-based object storage service provided by Amazon Web Services (AWS). It is designed to store and retrieve large amounts of data with high durability, scalability, and availability. Here are some key features of AWS S3:
- Objects: S3 stores data as objects, which can be up to 5 terabytes in size. Each object is identified by a unique key within a bucket.
- Buckets: S3 stores objects in buckets, which are containers for objects. Each bucket has a unique name and can be located in a specific AWS region.
- Durability: S3 provides 99.999999999% (11 nines) of data durability, meaning that it is highly unlikely that data will be lost or corrupted.
- Availability: S3 provides high availability, ensuring that objects can be accessed from anywhere in the world with low latency.
- Security: S3 supports several security features, including server-side encryption, client-side encryption, access control policies, and bucket policies.
- Versioning: S3 supports versioning, which allows you to track changes to objects over time and restore previous versions if necessary.
- Lifecycle policies: S3 supports lifecycle policies, which allow you to automatically transition objects to different storage classes or delete them after a specified time period.
- Replication: S3 supports cross-region replication, which allows you to replicate data between S3 buckets in different regions for disaster recovery and compliance purposes.
Related: This blog has information on how to get started with your Cloud Accounts and credits for free.
Let us now talk about some of the common mistakes you can make while using AWS S3.
Not Using Versioning
Versioning is a feature in AWS S3 that allows you to keep multiple versions of an object in the same bucket. This helps you to recover from accidental deletion or overwriting of objects. If you do not enable versioning, you risk losing your data permanently if someone accidentally deletes or overwrites it.
Versioning also helps with accidental overwriting of objects. Overwriting objects in AWS S3 is a common mistake that can result in data loss. If you overwrite an object with a new version, the old version is permanently deleted, and there is no way to recover it. To avoid this, enable versioning and use a unique name for each object.
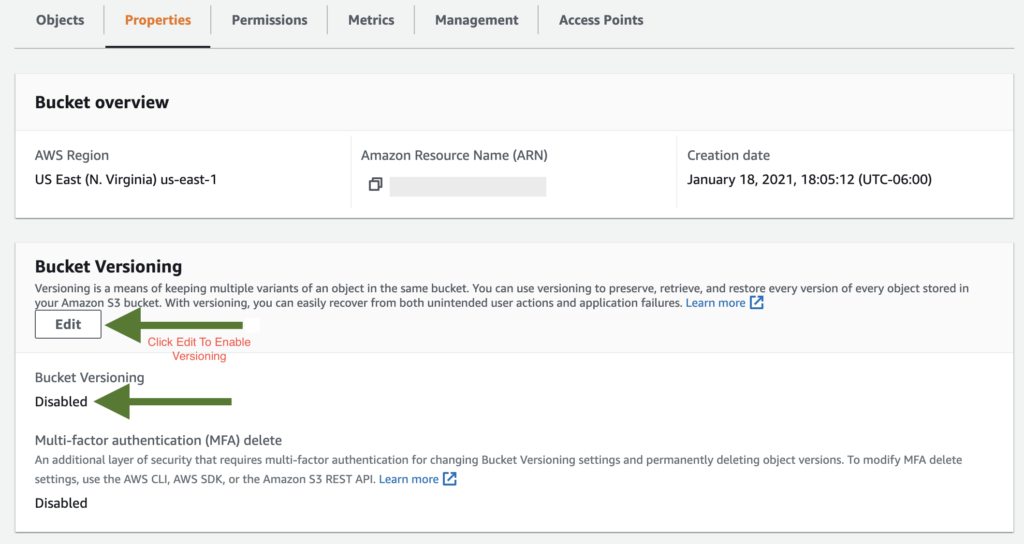
To enable versioning, go to the AWS console, select the S3 bucket you want to enable versioning on, and click on Properties > Versioning. Click on Edit and Enable versioning.
Using Public Access
One of the most common mistakes users make when using AWS S3 is allowing public access to their buckets. If the access is public at the bucket level, the chances of your data getting compromised is pretty high. This can happen when the bucket policy or object ACL is set to allow public access. Although, there might be use use cases where you’d want your bucket public.
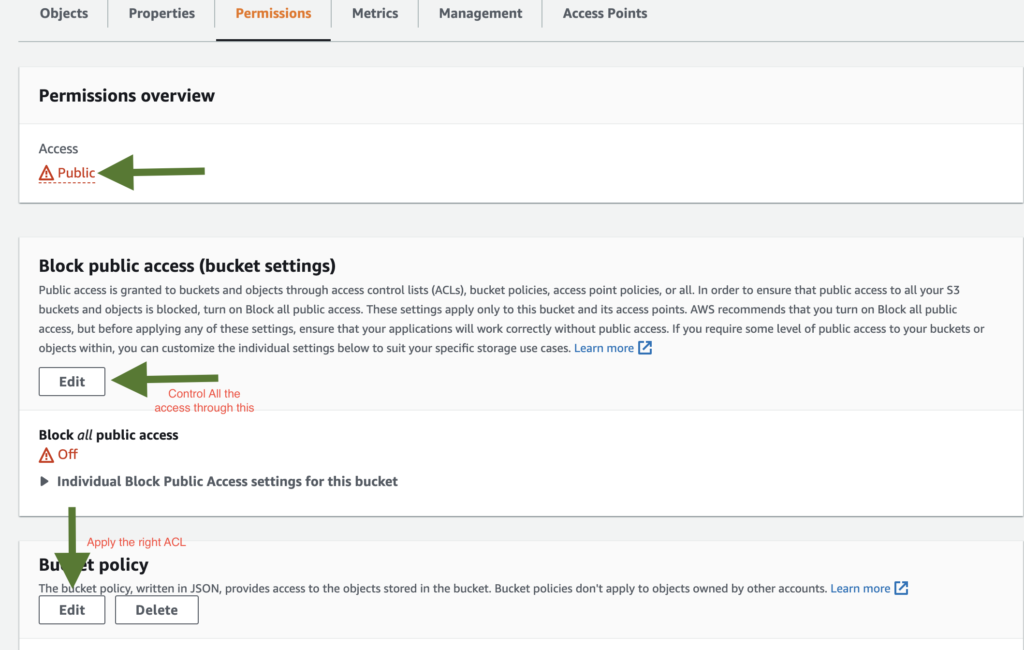
To avoid this, ensure that your bucket policy and object ACL only allow access to authorized users and accounts. The bucket can be made secure by clicking on the permission tab and applying the right ACL.
Not Encrypting Data
Encryption is essential for protecting sensitive data stored in AWS S3. If you do not encrypt your data, it can be accessed by anyone who gains access to your bucket. AWS S3 supports server-side encryption using AWS-managed keys, customer-provided keys, or KMS-managed keys.
To enable encryption, go to the S3 console, select the bucket you want to encrypt, and click on Properties > Default encryption.
Not Monitoring Bucket Activity
Monitoring bucket activity is essential for detecting unauthorized access or unusual activity in your bucket. AWS S3 provides several tools for monitoring, including CloudTrail, S3 Access Logs, and S3 Inventory. These tools allow you to track who is accessing your bucket, what they are doing, and when they are doing it.
To enable this, select the bucket you want monitoring for. Click on Properties > AWS CloudTrail data events.
Not Setting Object Lifecycle Policies
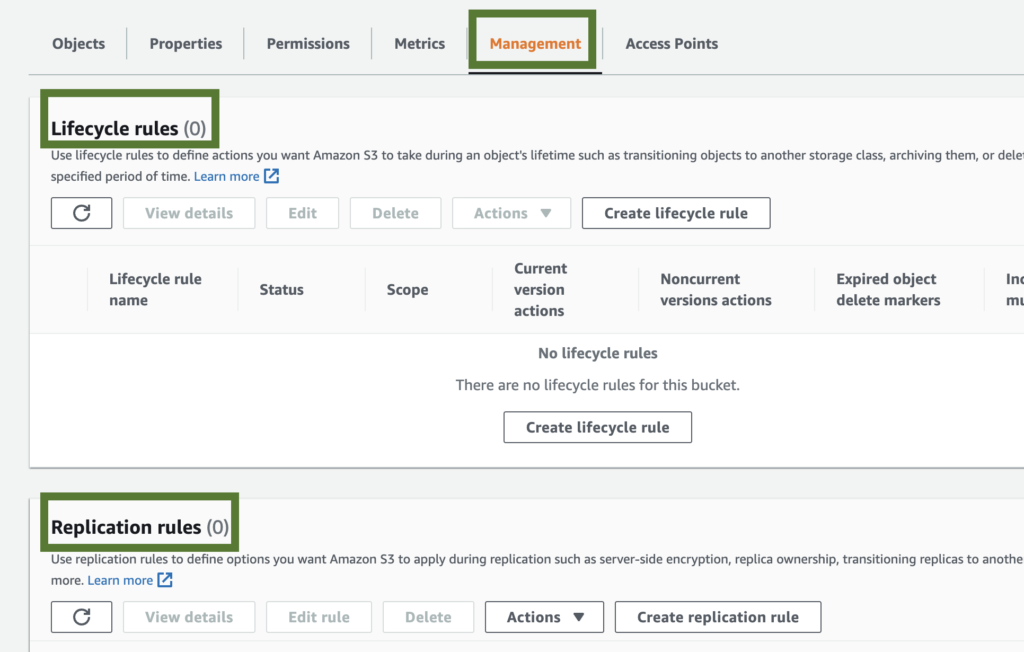
Object lifecycle policies are used to automate the management of objects in your bucket. They can be used to automatically move objects to different storage classes or delete them when they are no longer needed. Not setting object lifecycle policies can result in increased storage costs and a cluttered bucket.
To set object lifecycle policies, go to the S3 console, select the bucket you want to set policies on, and click on Management > Lifecycle Rules.
Not Using Cross-Region Replication
Cross-Region Replication is a feature in AWS S3 that allows you to replicate objects from one bucket to another in a different region. Although the durability of AWS is 11 9’s, cross region replication is essential for disaster recovery and high availability. Not using Cross-Region Replication can result in data loss or extended downtime in the event of a disaster.
To set up Cross-Region Replication, go to the S3 console, select the source bucket, and click on Management > Replication Rules.
Not Using MFA Delete
MFA Delete is a feature in AWS S3 that requires multi-factor authentication before objects can be deleted. This is an essential security measure that helps to prevent accidental or malicious deletion of objects. Not using MFA Delete can result in data loss or unauthorized deletion of objects.
To use MFA delete with versioning, you enable MFA Delete. However, you cannot enable MFA Delete using the AWS Management Console. You must use the AWS Command Line Interface (AWS CLI) or the API.
Conclusion
Misconfigured S3 buckets are a recipe for disaster and can cause brand damage to the organizations in case of data leaks. There should be a regular sweep of the AWS buckets along with processes developed to handle any security vulnerability. Developers should ensure that proper S3 bucket policies are applied to make the data secure and highly available.
Further Reading:
Check out the noteworthy differences and similarities between AWS and Azure in this blog.

